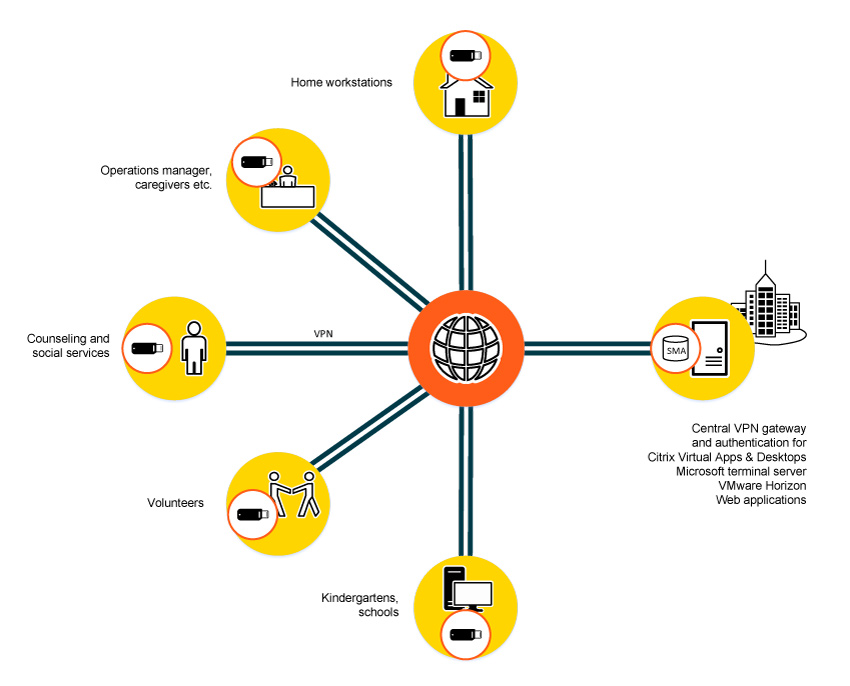
Remote access for social service facilities
Making working hours and work locations more flexible while reducing costs is no longer limited to the private sector, it is a growing issue for social services institutions too.
It is therefore essential to give these organizations external access to their data and applications.
With the right technology, even the highest data protection and data security requirements can be met for remote data access.

Outpatient care
Caregivers have to report their care activities. Instead of returning to the care facility, it is be clearly easier for them to complete their reports at home in the evening. Not only does it contribute to increase motivation and commitment of employees, it also distinctly reduces travel expenses.
Operations managers often have to update duty rosters and route planning on weekends because of emergencies and unforeseen events. Therefore, both operations managers and caregivers need fast and flexible access to their facility's administrative systems.
From a budget perspective, it makes sense to allow the use of private PCs for such activities while considering data protection and data security requirements without placing an additional burden on IT.

Home office
In order to promote families and retain experienced employees, offering mothers-to-be and parents with small children a better work-life balance is a worthwhile investment.
Private PCs can be used as workstations without security concerns while ensuring 100% separation of private and professional use.

Kindergartens and schools
Appropriate security arrangements must be made for educators' and teachers' access to administrative systems, especially because development reports or report cards involve very personal data.
If a PC is also used to surf the internet, the access to illegal or age-inappropriate contents must be prohibited.
The right solution for any requirement
![ECOS SECURE BOOT STICK [CL] Secure Boot Stick CL ist übergroß vor aufgeklapptem Macbook platziert](/fileadmin/ecos/01_pictures/04_products_500x330/CL_01.jpg)
Secure Boot Stick CL
Hardened ECOS Secure Linux operating system
All software on the stick
2-factor authentication w/ software certificate
Integrated firewall
Central management
![ECOS SECURE BOOT STICK [HE] Abbild von silbernem Secure Boot Stick HE](/fileadmin/ecos/01_pictures/04_products_500x330/HE_01.jpg)
Secure Boot Stick HE
Hardened ECOS Secure Linux OS
All software on one stick
2-factor authentication w/
software certificate
Integrated firewall
Central management
Hardware-encrypted security
2-factor authentication w/
hardware anchor
BSI-approved
![ECOS SECURE BOOT STICK [FX] Produkt Nahaufnahme des Secure Boot Stick FX](/fileadmin/ecos/01_pictures/04_products_500x330/SECURE_BOOT_STICK_FX.jpg)
Secure Boot Stick SX
BSI-approved for VS-NfD,
EU and NATO RESTRICTED
Highly secure VS-NfD access w/
genua genuscreen
Sealed stick environment
Extra hardened ECOS Secure Linux
Multi-factor authentication w/
smartcard
Keypad for PIN entry
Central management and remote
updating