Trusted Identities – for every machine, every device, every agent
Secure machine identities Industrial cybersecurity for your OT infrastructure
The digital transformation is reshaping traditional production environments (OT) into highly networked, intelligent ecosystems – from SCADA systems and PLCs to field devices and sensors. This connectivity brings enormous efficiency gains, but also new entry points for cyberattacks.
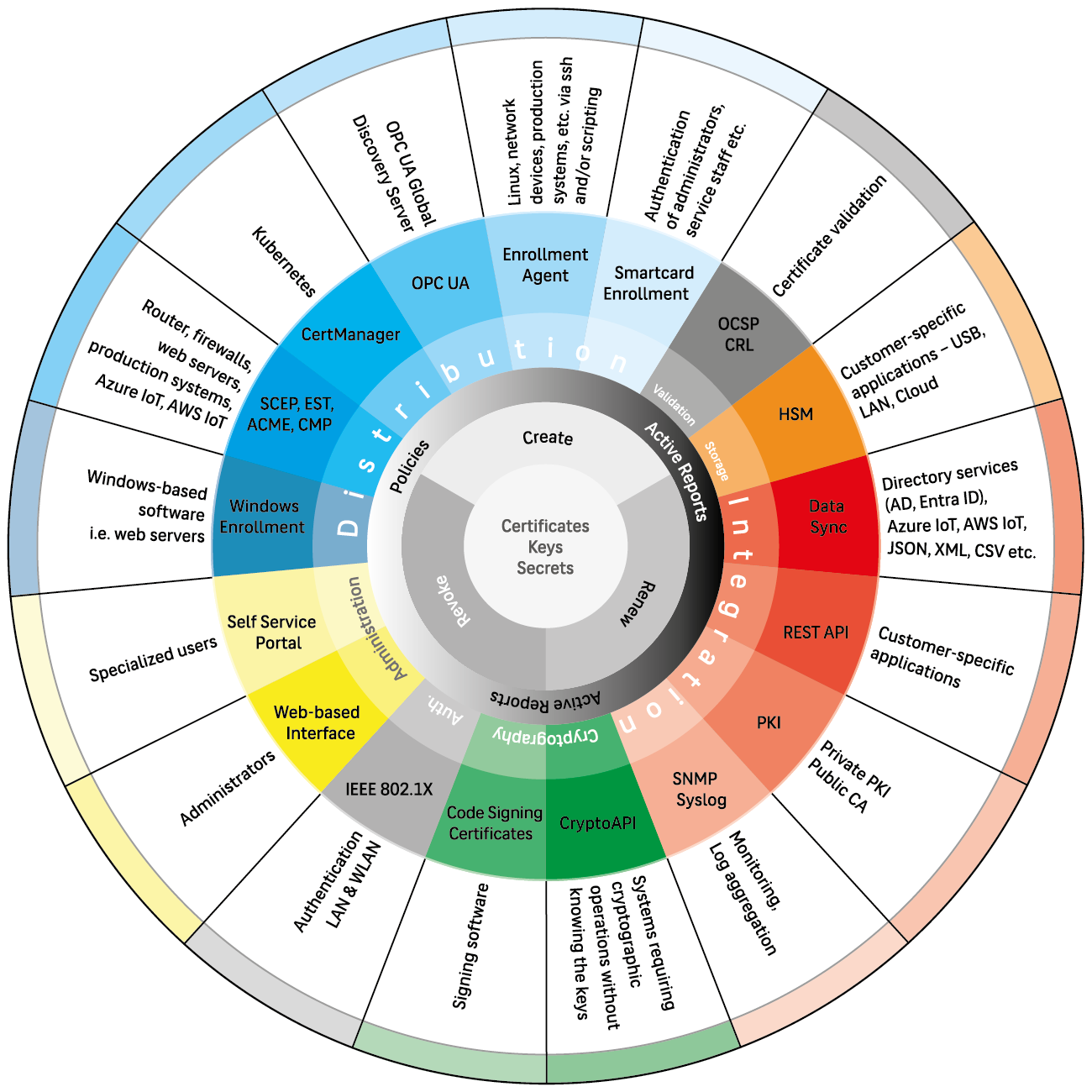
The ECOS TrustManagementAppliance® addresses these challenges by acting as a central PKI and key management system for OT infrastructures and creating the basis for industrial cybersecurity with secure identities.
As AI agents increasingly take on autonomous tasks in industry – from predictive maintenance and process optimization to autonomous control systems – they, too, must be authenticated beyond doubt.
The TMA assigns unique, verifiable identities to AI agents, ensuring data integrity, preventing manipulation, and enabling secure integration into Zero Trust architectures.
With the ECOS TrustManagementAppliance®, industrial organizations create a future-proof trust framework that protects machines, systems, and AI-driven processes alike.
- Central basis of trust for OT security
Trusted machine identities for all components from actuators/sensors to PLCs, SCADA systems, and ERP – ensuring verifiable authenticity and integrity. - High availability and flexibility
Deployable on-premises, in the cloud or hybrid without impacting running production operations. - Heterogeneous protocol support
Compatible with classic components and modern standards such as OPC UA with integrated security mechanisms. Simple integration
API-based connection to OT and IT systems (e.g. HSM, IAM, SIEM) for seamless embedding into security and automation infrastructures.
- Automated certificate management
Fully automated issuance, distribution, renewal, and revocation — compliant, transparent, and efficient. - Future-proof and compliance-ready
Crypto-agile and designed to support security-by-design principles and evolving regulatory requirements. - Basis for zero-trust architectures in OT
Creation of a consistent security concept even in complex and distributed production environments through trusted digital identities. - Identities for AI agents
Authenticate AI instances uniquely in production or service and embed them securely into zero-trust workflows.
ECOS TrustManagementAppliance®
The foundation for digital trust in IoT, OT and AI
The ECOS TrustManagementAppliance® creates, distributes and manages digital certificates and cryptographic keys that assign trusted identities to devices, systems and AI agents. These secure machine identities form the foundation for protecting data, processes and autonomous decisions — and are therefore essential for a secure, scalable and future-proof industry.
The ECOS TrustManagementAppliance® can be operated on-premises, in the cloud, or managed as a service by ECOS.